Pakistan is currently testing its firewall systems, and the second phase of its installation was recently completed successfully. A firewall is essentially a computer network security system that regulates internet traffic entering or exiting a network. It works by either blocking or allowing data packets (traffic) based on pre-defined rules. The primary purpose is to help prevent malicious activities and unauthorized access to private networks.
What is a Firewall?
Firewalls act like gated borders or gateways, controlling activities within a private network. The term “firewall” is borrowed from barriers designed to prevent the spread of fire. Just as these walls help contain and extinguish fires, network security firewalls manage web traffic to minimize risks. They create ‘choke points’ where traffic is examined according to programmed parameters and then allowed or blocked accordingly. Some firewalls also have the capability to track traffic and connections in audit logs.
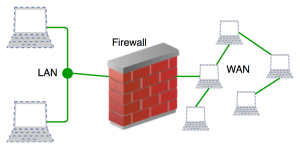
How Does a Firewall Work?
A firewall determines which network traffic is safe to pass through and which is potentially harmful. Essentially, it filters content by distinguishing between trustworthy and untrustworthy data. The goal of firewalls is to secure networks and the endpoint devices within them, known as network hosts.
Types of Firewalls
There are various types of firewalls, each utilizing different filtering methods. They can be classified based on their operating mechanisms, such as connection tracking, filtering rules, and audit logs.
- Static Packet Filtering Firewall Also known as stateless inspection firewalls, these operate at the OSI network layer (Layer 3). They provide basic filtering by examining each individual data packet sent across the network, determining its source and destination. The filtering is based on IP addresses, ports, and packet protocols, and it prevents unauthorized direct connections between at least two networks. While effective for small networks, they are challenging to operate on larger ones. Additionally, these firewalls cannot read application protocols, meaning they cannot inspect the contents of messages within the packets. Due to this limitation, they are considered less robust.
- Circuit-Level Gateway Firewall Operating at the session level (Layer 5), these firewalls inspect the functional packets within a connection and, once a connection is deemed secure, allow it to remain open between two networks. After establishing the connection, the firewall stops monitoring it, potentially allowing malicious data to enter unchecked.
- Stateful Inspection Firewall Also known as dynamic packet filtering firewalls, these are unique due to their ability to monitor ongoing connections and remember past connections. Initially operating at the communication layer (Layer 4), these firewalls now monitor multiple layers, including the application layer (Layer 7). Layer 7 monitoring allows the firewall to analyze and filter traffic based on specific applications rather than just IP addresses and ports. This firewall updates filtering rules based on login history recorded in a state table by the screening router. While the initial filtering decisions are often based on administrator rules, the state table enables these dynamic firewalls to make their own decisions, such as filtering traffic types that have caused issues in the past.
- Proxy Firewall Known as application-level firewalls (Layer 7), proxy firewalls can read and filter application protocols. They combine application-level inspection or ‘deep packet inspection (DPI)’ with stateful inspection. Unlike other firewalls, proxy firewalls act as separate representatives (or proxies) between external networks and internal computers. They function like a physical barrier, examining incoming data at the gate, and only allowing it to pass if no threats are detected. However, the downside of this high level of security is that it can sometimes interfere with non-threatening incoming data, causing disruptions in the network.
- Next-Generation Firewall (NGFW) As emerging threats demand new solutions, these firewalls stand out by combining the features of traditional firewalls with network intrusion prevention systems. They are leading the way in combating modern threats.
- Hybrid Firewall As the name suggests, hybrid firewalls use a combination of two or more firewalls within a private network.
Real-World Examples and Key Incidents
In practice, the real-world application of firewalls has attracted both praise and controversy. While firewalls have a long history of success, they must be implemented correctly to avoid exploitation. Additionally, firewalls have been used in ethically questionable ways.
- China’s Great Firewall and Internet Censorship Since 2000, China has maintained an internal firewall framework for internet use within the country. This system allows the Chinese government to restrict internet services to local companies, making it easier to control things like search engines and email services.
- U.S. Federal Agency Cyberattack In 2020, a misconfigured firewall led to a cyberattack on a U.S. federal agency’s network.
- U.S. Power Grid Incident In 2019, a U.S. power grid was affected by a Denial-of-Service (DoS) attack, which hackers exploited. The perimeter network firewalls were stuck in a reboot loop for nearly ten hours, later attributed to a vulnerability in the firewalls. These incidents highlight the importance of regular software updates. Without them, a firewall—a critical network security system—can become a significant vulnerability.





 United states Playing Income tax in...
United states Playing Income tax in...